CONFIGURING YOUR SECURITY GROUPS AND FIREWALL RULES
INTRODUCTION
Security groups are like firewall rules for the AWS cloud. For help with configuring your security groups, please consult the AWS guide found at http://docs.aws.amazon.com/AmazonVPC/latest/GettingStartedGuide/SecurityGroup.html.
WANROCKIT PORTS
All rules are inbound; “Outbound” should be open globally to all traffic (default in AWS).
The following table lists the ports and protocols that you might need to open on your WANrockIT Node’s security group, and a description of what each is used for.
| Protocol/Port | Description | Recommended Source |
| TCP 22 | SSH, used for accessing the Command Line Interface (CLI) | “My IP” |
| TCP 80 | HTTP, used for accessing the Web Interface unencrypted | “My IP” |
| TCP 443 | HTTPS, used for accessing the Web Interface encrypted | “My IP” |
| TCP 16665 | WANrockIT main transfer port | WAN interface IP of connected Node |
| UDP 4500 | IPsec, used for encrypting WANrockIT traffic | WAN interface IP of connected Node |
| UDP 500 | IPsec, used for encrypting WANrockIT traffic | WAN interface IP of connected Node |
| ESP | IPsec, used for encrypting WANrockIT traffic | WAN interface IP of connected Node |
The last column in the “Add Rule” dialog is the “Source”. This decides the range of IPs, or security group, from which the “Port Range” for each rule is accessible. This is done in CIDR notation, in the form “x.x.x.x/xx”, or by security group ID, in the form “sg-xxxxxxxx”. Multiple sources can be specified for a rule using comma separation.
The source can be left as “Anywhere”, although it is highly recommended to set the source to a limited IP address range or specific security group.
- TCP Ports 80, 443 and 22 should be set to use the source IP address of the network(s) from which you wish to manage your Node. An easy method of doing this is to select “My IP” from the drop-down.
- TCP Port 16665, UDP Port 4500, UDP port 500 and ESP should be set to use the IP address of your on-premise/CSP Node. For example, if your local network has a single static IP address of 80.106.67.84 then you should set the source IP address to be 80.106.67.84/32. If your Nodes are connected over a VPN, the IP address of your on-premise/CSP WAN port should be used instead.
PROTOCOL-SPECIFIC PORTS, OS LEVEL FIREWALL RULES AND COMBINING SECURITY GROUPS
The following ports are used by your AWS WANrockIT Node to communicate with iSCSI/FTP hosts and targets within the same local network.
If your Node has been added to the security group used by your hosts and targets, they should already be able to communicate, and no further rules need to be added. If not, some of the following rules should be added to the Node’s security group, depending on the protocols you are using.
| Protocol/Port | Description | Recommended Source |
| All TCP | FTP command & data transfer | FTP server security group |
| TCP 3260 | Port used for iSCSI traffic | iSCSI initiator/target security group |
| TCP 860 | Alternate port used for iSCSI traffic | iSCSI initiator/target security group |
Depending your client/server setup, FTP may use a wide range of ports. If you don’t know what these are, it’s best to allow all TCP ports.
The port numbers for iSCSI will be different if using custom ports on your Node/host.
These ports will also have to be added to firewall rules on your hosts. For example if using an FTP server on a Windows 2012 server instance, the firewall rule allowing TCP port 21, plus the range used for data transfer, will have to be added to the list of custom “Inbound Rules”. For a detailed article on how to set up firewall rules on a Windows server please see the following Microsoft support article:
https://technet.microsoft.com/en-us/library/cc753558.aspx
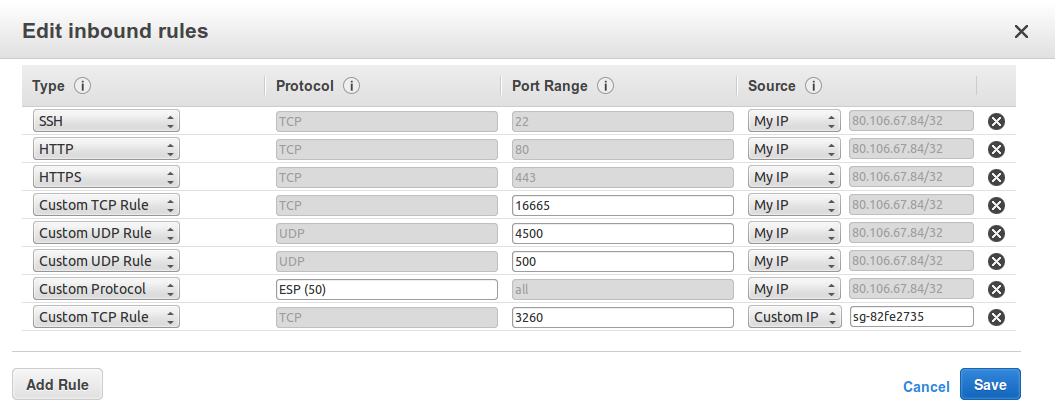
EXAMPLE SECURITY GROUP
The following screenshot shows an example security group for a Node which is connected to iSCSI targets belonging to the security group “sg-82fe2735″. The WAN link is established using public IP addresses, and IPsec is enabled. The Node is being administered from the same network as the on-prem Node is located (80.106.67.84).

Bridgeworks have looked at the problem of data movement and come at it from an entirely new perspective. In mastering the rules of data movement over distance, Bridgeworks have now broken them to provide you with the ability to move significant volumes of business critical data in real time removing unacceptable time lags, that risk failure, delay or presents major costs to your business.
